TAM Documentation - How to set up Azure AD Authentication / Single Sign-On
Here is a describtion of what the TAM needs to ask the customer for, to be able to enable Azure AD Authentication/ Single Sing-on on Link platforms
Setup Link User Groups & Azure AD Groups
When a user logs in to Link for the first time using Azure AD authentication, Link will create a new user and assign one or more user groups. Which groups depends on what AD groups the user is member of. On a link user group it's possible to specify a Domain Account. If a user has an AD group with that name the user group will be assigned to the user.
NOTE: Link will synchronize Azure AD groups every time a user logs on. Any assigned Link-groups, that are not found in Azure AD will be removed from the user.
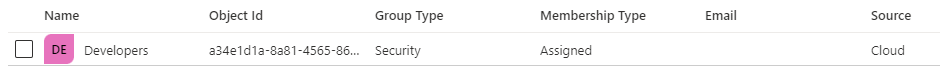
A users group memberships in Azure AD: (Must be created by the Customers IT department)
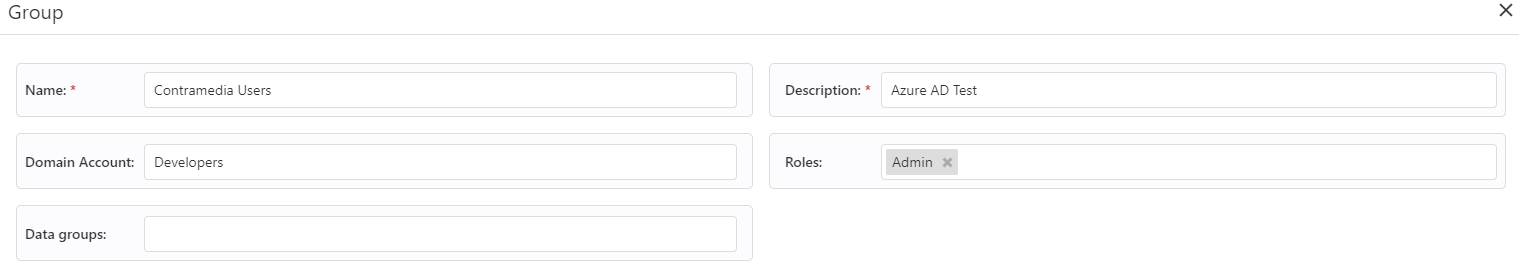
A matching group in Link: (Must be created/edited by the TAM of the customer)
The TAM’s needs to ask their customer to create these 3 default Azure AD groups (naming standard is decided by the customer:
Admin
Editor
Viewer
Now the TAM has to create groups in Link in the customers dataowner, and then link the domain account to the groups made in Azure AD.
NOTE: If the Azure AD group is synchronized from Windows AD, Domain account name might need to be prefixed with the Domain name eg: DOMAIN\Admin
NOTE: The Link user will be granted access based on what role the Link user group has.
As you can see from the screenshots above the Azure AD group “Developers” has been made, and the Link user group “Contramedia Users” has been made, and the Azure AD group has been added to the Link group under the “Domain Account” section.
This is what must be performed for each of the 3 groups mentioned above.
Customer login process
The Link login dialog should now look like this:
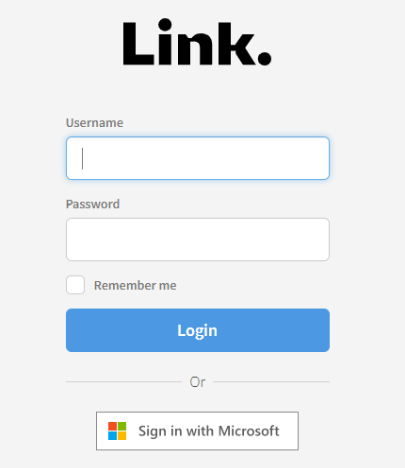
Click Sign in with Microsoft and enter your credentials (the customer must peform this step)
If the customer is met with a window that says that this application needs to be approved, just know that this is a security measure on the customer side, and not Bizbrains.
They must ask their IT staff permission to approve Link as an enterprise application in their Azure AD.The first time the customer sign in they will be met with the screenshot below. When they see that notification they need to let the TAM know. The TAM then has to provide their Dataowner ID to Operations as well as letting Operations know,
that the customer is ready for Azure AD Authentication/Single sign-on on Link. Create a Wrike request with the information, and Operations will handle it and get back to you, once access has been given.
Additional steps for troubleshooting
Based on previous experiences setting up Azure AD SSO Authentication the following steps can be checked for troubleshooting:
Explicitly stated emails in AD
Although a user might have their username set to the same value as their email address, it is still necessary to explicitly state/insert an email address on the Azure AD user. This is needed since Link requires an email address on a user, and without this explicitly stated, Link considers the user/creation of the user as invalid
Check that the "ADAuthentication_CreateUser_DefaultInternalPartner"-key
Ensure that the "ADAuthentication_CreateUser_DefaultInternalPartner"-key is set up correctly with the correct partner ID of the internal default partner. The PartnerID can be found in the URL when you are looking at the internal partner. The "ADAuthentication_CreateUser_DefaultInternalPartner"-key can be set by selecting the “Settings”-tab and then the “DataOwner settings” options.